Online Security
We hope to answer any concerns you may have about the security of managing your insurance online.
TUI UK Limited trading as TUI arranges travel insurance underwritten by AXA Insurance UK Plc. TUI UK Limited is an Appointed Representative of AXA Partners UK Plc which is authorised by the Prudential Regulation Authority and regulated by the Financial Conduct Authority and the Prudential Regulation Authority. In this online security statement “our”, “we” and “us” refer to AXA Insurance.
Click on the following options to find out more:
We have also put together a security glossary to help you understand abbreviations and jargon.
axainsurance.com uses the most up-to-date encryption technology available. To make sure it works the best it can for you, use a recommended internet browser (such as Microsoft Internet Explorer and Firefox) as they also offer the latest encryption technology.
All information you share with us is held in the strictest confidence, in compliance with privacy standards followed by all major British financial institutions. You are the only one who can access your policies, using your password and email address.
We are also registered with Thawte, a leading Internet Security Company. To verify our site security, click on the Thawte Trusted Site Seal shown below and this will show you our certificate. This is proof of our commitment to your security.
We also support MasterCard SecureCode and Verified by Visa. These are extra security measures introduced to ensure your details are secure when shopping with us. Once you enter your bank details and click NEXT on our website you will then see a Mastercard or Visa additional security page. For more information just click on the images below.
If you pay for your insurance with us by credit card, you will also have the extra protection of the Consumer Credit Act. Your maximum liability of your credit card is £50 if it is lost or stolen or used fraudulently and your liability stops as soon as you tell your credit card company what has happened.
We are also covered by the Financial Services Compensation Scheme (FSCS). In the unlikely event that an insurance provider goes out of business or into liquidation, you may be entitled to compensation from the scheme. This would take place if the FSCS is not able to transfer your policy to another insurer or provide a new policy. Compensation amounts depend on the type of insurance and the circumstances of the claim. Further information is available from the FSCS at 7th Floor Lloyds Chambers, Portsoken Street, London, E1 8BN. Tel: 020 7892 7300 or via www.fscs.org.uk.
Should you need to call us, we may record your call to offer you extra security, resolve complaints and improve our service standards.
Confirming it is axa.com
How can I be sure I am using a secure axa.com website?
When you enter personal information onto our website, make sure it encrypts the information you send to, and receive from, the site.
Always ensure the spelling of the domain name is correct.
Make sure the URL begins with "https" rather than "http".
For Internet Explorer 7 & 8 and Firefox 2 & 3 users you should find a padlock icon located next to the URL on the top right. For Internet Explorer 6 and Safari 2 you will find the icon located on the bottom right of the browser window.
Make sure the domain is owned by the company you expect to interact with by double-clicking on the lock icon in your browser. The key to look for is that the domain axainsurance.com in the following example is present.
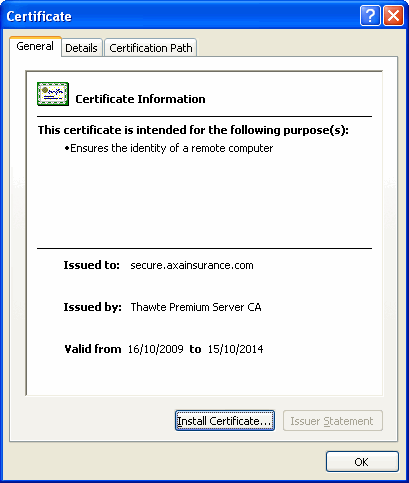
E.g. secure.axainsurance.com = (subdomain=secure).(domain=axainsurance).(top-level domain=com)
Security Glossary
Antivirus software
These are programs to detect and remove computer viruses. The simplest will scan executable files and block a list of known viruses. Others are constantly active to detect viruses and find out what they are doing. Antivirus software should always include a regular update service to detect the latest viruses as they are released. For more information visit the Antivirus section.
Back door
A hardware or software-based hidden entrance to a computer system that can be used to bypass the system's security. For more information take a look at the Antivirus section.
Cookies
Cookies are small files stored on a computer's hard drive and are generally harmless. They are used to recognise you so that you receive a more consistent website experience. Cookies can contain information about your preferences that allows a site to provide a more personal service.
Encryption
Encryption converts your data into an encoded form before it is sent over the Internet, stopping unauthorised users from reading the information. At axainsurance.com, we use 128-bit Secure Socket Layer (SSL) Encryption which is accepted as the industry norm. You know that your session is in a secure encrypted environment when you see https:// in the web address, and/or when you see the locked padlock symbol.
Firewall
A firewall helps protect your computer and its contents from outsiders on the Internet or network by stopping unauthorised traffic to and from your PC. Common examples are from Zone Labs, Symantec (Norton), McAfee and Computer Associates. In many cases there is a version of commercial software that is free of charge for personal users. For more information visit the Personal firewalls section.
Keystroke capturing and logging
Anything you type on a computer can be captured and stored via a hardware device attached to the PC or by software running almost invisibly on the machine. Keystroke logging is often used by fraudsters to capture personal details including passwords. Some recent viruses can install such software without the user's knowledge. The risk of keystroke logging is greater on PCs shared by a number of users (such as Internet cafes). Running anti-spyware software would help and can be downloaded free. For more information visit our Spyware Removal section.
Phishing
A phisher is a malicious user or Web site that deceives people into revealing personal information such as passwords and credit card numbers. They usually use e-mail messages or online advertisements linked to fraudulent Web sites where the users are then tricked into providing personal information. Confirming it is axainsurance.com section.
Secure sessions
When you log in to axainsurance.com you are in a secure session. SSL technology is used to encrypt information before it leaves your computer to ensure no one else can read it. Depending on your browser settings, a pop-up window may appear to let you know you will be entering a secure page. You will know that you are on a secure page when you see the 'https://' before the web address. You will also see a closed padlock symbol in the lower right hand corner of your browser window.
Secure Sockets Layer (SSL)
Secure Socket Layer (SSL) protocol provides a high level of Internet security by ensuring an encrypted communications session between your web browser and a web server. SSL helps to ensure that sensitive information (e.g. credit card numbers) sent over the Internet between your browser and a web server remains confidential during online transactions.
Session time-outs
These are automatic disconnections, for security reasons, from any secure session after a period of server inactivity. It may occur even if you are typing something into a page or data field, the event being triggered by no communications to our servers, rather than by keyboard or mouse inactivity. All our online services have this protection.
Spyware
This is software that gathers your information through your Internet connection without your knowledge, usually for advertising purposes. Spyware applications are typically bundled as a hidden component of programs that can be downloaded from the Internet. Once installed, the spyware monitors your Internet activity and transmits that information in the background to someone else. Spyware can also gather information about e-mail addresses and even passwords and credit card numbers. Spyware is similar to a Trojan horse in that customers unwittingly install the product when they install something else. A common way to become a victim of spyware is to download certain peer-to-peer file swapping products that are available today. For more information visit the Spyware Removal section.
Trojan horse
A destructive program that masquerades as a harmless application. Unlike viruses, Trojan horses do not copy themselves but they can be just as destructive. One of the worst types of Trojan horse is a program that claims to rid your computer of viruses but instead introduces them.
Virus
A computer program usually hidden within another program that produces copies of itself and inserts them into other programs to perform a malicious action (such as destroying data).
Vulnerability
Security holes/bugs are faults, defects or programming errors. These may be exploited by unauthorised users to access computer networks or web servers from the Internet. As these vulnerabilities become known, software publishers develop patches, fixes or updates that you can download to fix the problems. For more information visit the Updating your computer section.
Worm
A worm is a program that replicates and spreads throughout a computer system. It will usually hide within files and distribute those files through any available network connections. In addition, worms can spread rapidly via email. For more information visit our Antivirus section.
Antivirus Software
You may already be using antivirus software but to be effective the software should be updated on a regular basis with the latest virus definition files. If you are unsure how to do this, you should refer to the program's Help function. There are many effective programs to choose from but the most common commercial products include* (in alphabetical order):
- AVAST
- AVG
- Kaspersky Labs
- Norman
- McAfee
- Panda
- Symantec
- Sophos
- Trend Micro
Spyware Removal Software
You may already be using spyware removal software but to be effective the software should be updated on a regular basis with the latest reference files. There are many effective programs to choose from but the most common commercial products include* (in alphabetical order):
- Lavasoft Ad-aware
- Spybot-Search & Destroy
- Spy Sweeper
Personal Firewalls
A firewall is another small program that helps protect your computer and its contents from outsiders on the Internet and stops unauthorised traffic to and from your PC. There are many effective programs to choose from but the most common commercial products include* (in alphabetical order):
- BlackICE Defender
- Kerio Personal Firewall
- McAfee Personal Firewall
- Sygate Personal Firewall
- Norton Personal Firewall
- Tiny Personal Firewall
- Zone Alarm
Updating your Computer
Hackers and/or viruses discover weaknesses in software that allows them to gain access to your computer. In order to prevent such attacks and protect your computer, software developers offer free updates for their software via their websites.
To check for updates, simply visit the publisher's website, typically in their Download section, for example:
- For Microsoft Windows users visit Microsoft Windows update
- For Apple Macintosh users visit Apple service and support
If you have an earlier version of a browser, it's easy to download an updated version:
- For Internet Explorer: Click on the free Downloads link on the Microsoft site at www.microsoft.com/ie
- For Firefox: Click on the free Downloads link on the Mozilla site at firefox.com/
- For Safari on Mac OS X: Click on the free Downloads link at the Apple site at www.apple.com/safari/
* The list of suppliers is given for information only and should not be taken as recommendations by axainsurance.com. If you are unsure of suitability, you should seek expert advice. Further information can be found by using Internet search engines on antivirus software and spyware.







